We probably all use browser extensions, whether it's a coupon code extension, something that checks your grammar, or a password manager. Well, I hope you trust whoever runs it because extensions can be a lot more dangerous than people realize. Conventional wisdom says - "Just check the permissions of an extension before installing it", but if you were shown those permissions would you really understand what they meant?
What are Browser Extensions?
Browser Extension is a small piece of software that adds functionality or features to a web browser. They're designed to enhance the user experience or extend the capabilities of the browser. Browser extensions interact with web browsers by using a set of special communication rules called APIs that allow the extension to change or improve how you view and interact with the web pages. They're strictly controlled APIs which in theory means that they have specific limitations in place to ensure that the extension is safe and secure for the users.
Components that can make an Extension :
Background Service Workers
The background script is a service worker that runs in the background. The service worker is simply a container to run codes, it's all hidden from the user with no visual indication that there's code running, and you can't really inspect its network activity. Checking up the network activity for a normal website is easy while a background worker's network activity for extensions is really hard to get to, you can have a look at the below pictures.
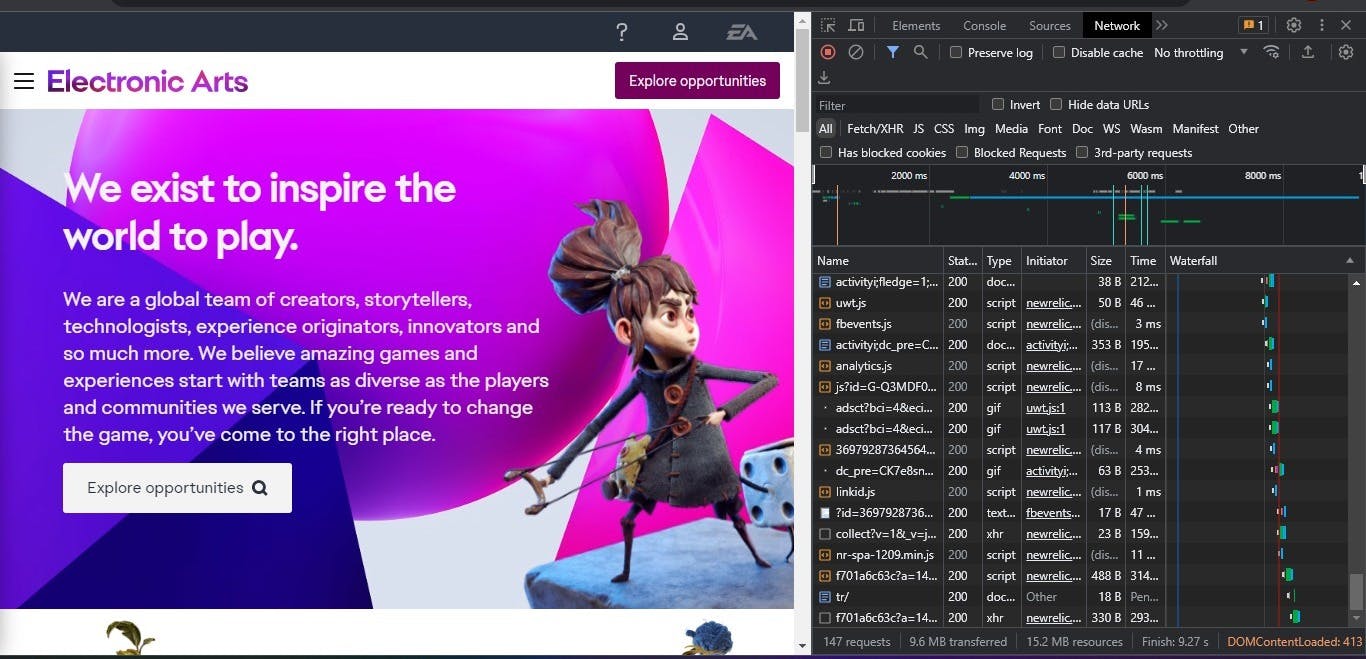
Here in the case of a normal website, you can see how simply I've displayed the network activity from the developer console.
Pop-ups
Pop-ups are useful for certain tasks that need a user interface. The popup is one of the native user interfaces that the extension can use. It renders an extension webpage every time, so that's your user interface. Certain activities can only be performed using the user interface so popups are a handy tool.
Content Scripts
They are one of the worst offenders, you can use them to inject JavaScript and CSS into the page. In practical terms, you can use them to build something that paints on top of the page, or make modifications to the page, there are no limits this is where you can gather most information from the page. You can also set listeners for anything the user is doing like keystrokes, mouse movements or reading inputs. So that's the component that can do the most damage.
Some specific permissions an there nature that we need to know about -
History Permission: The browser will happily dump out your history as an array, which contains all your browsing history, frequently visited sites and much more which can then be used to create a profile of yours. So literally the extension can get your complete browsing history and use it however they want.
Cookies Permission: Some extensions can call out a single line of JavaScript to dump out all your cookies with associated domains, that's how the browser authenticates with the servers. If someone steals your cookies they can pretend to be you in some sort of nasty way. One of the most subscribed tech channels - Linus Tech Tips with more than 15 Million subscribers was hacked by stealing his cookies.
Desktop Capture Permission: There are several APIs that an extension can use to capture your desktop and capture the current page you're looking at and all of these will incur a pop-up. Sometimes a tab capture is also used, the capture visible tab API- no warning and it just takes a screen grab and sends it off and you'll never know what's happening. For example, if you are on a banking website, they can a screenshot every second and send that off.
Web Request Permission: You can sniff the request going to every website and see what's it sending, On websites like stripe.com their security is immaculate, it doesn't matter I can see what you are sending to it. Anything that's watching the traffic, especially the payloads, that's pretty damaging.
Keyloggers: This one doesn't need permissions, you don't need any special keylogger permission to use one.

This content script technically called a host permission would create a pop-up that says- "Allow this extension to read everything on, say google.com". If it's able to see everything that you are searching, all your keystrokes or anything then it would send them to our background script which sends them to our server. None of them requires any permissions other than the ability to run that script on google.com.
Opening Tabs with extension: A major threat
A creative workaround being used by malicious actors for their sneaky purposes is opening tabs without the user knowing it, it may be referred to as stealth tabs. When so many tabs are opened up but are not in use, browsers usually unmount these idle tabs meaning pausing those that you haven't used in a while, If the browser decides that it's an idle tab it'll stop running javascript on the page, to save the battery and system resources, if you click into it the browser will bring it back up. Some of the extensions can identify such paused tabs, hijack them and repurpose them, They spoof what the tab originally looked like i.e. the little icon and the name so that to a user nothing seems to change, they'll never see that it just swapped up their tab as the spoofed one looks identical. It could send you to all kinds of malicious sites or collect your geolocation. If in case the user clicks on these idle tabs, they will go back to the original tab with the spoofed one leaving out for a while, all that they can understand is a usual page refresh.
Conclusion
As described above, there are some more disturbing things that extensions can do such as updating their code remotely this means that the code you thought you installed could be replaced with something else without you knowing it. Due to all these security reasons, it is highly recommended to read out all the Extension permissions carefully while granting them.
You should use reputable extensions like- Ublock Origin and Privacy Badger.
Trust projects that are built with consumer protection in mind, having very good developers maintaining it, more preferably with a huge open source community.
Some things you need to check like - Who owns the extension? Are they being maintained?
Do not blindly rely on anything just because it is open source as it might have the entire code base available on GitHub but actual code winding up with the browser is different.
Try to use in-browser features instead of extensions for some things, that could be one way to decrease your attack surface.
Reference - Building Browser Extensions by Matt Frisbie
Follow to read more such helpful and interesting articles and share them with everyone you know, try to make secure surfing a new normal. Feel free to give any suggestions for improvement.


